Ransomware Recovery in Singapore

As ransomware is an evolving problem in this technologically advanced world, organizations of all sizes are finding themselves investing in ways to prevent a ransomware attack. Those who have fallen prey to an attack will need to seek help in recovering their data. Unfortunately, ransomware is here to stay. Therefore, let us investigate how we can better protect our data.
What is Ransomware?
Ransomware is a type of malicious software (malware for short) that can restrict or block a user’s access to their files. Cybercriminals use this malware to hold the user’s important documents as “hostages” and demand a ransom in return for them – hence the term ransomware.
The concept behind ransomware is relatively simple. More often than not, a computer gets infected by ransomware after a user clicks on a malicious link or opens a suspicious attachment in an email. By doing so, the ransomware will secretly start encrypting the user’s data. Upon completion of the encryption, a ransomware note will appear on the user’s system, demanding payment in exchange for the decryption of that data. This ransom demand will usually be in Bitcoin, which is harder to trace, and typically has a cut-off time. If the cybercriminal does not receive the demanded ransom by the stipulated deadline, the ransom may increase. That said, it may not be a good idea to pay for the ransom either, as these cybercriminals may not decrypt the data after receiving the ransom. It is best to engage a professional ransomware recovery company to restore your data.
Types of Ransomware
There are two major types of ransomware: Crypto ransomware which usually involves encryption to prevent a user’s access to files or data; and Locker ransomware, which locks the user out of their computer or device.
Crypto ransomware is similar to the example stated above – where the user’s data is being encrypted and the user cannot use this data until it has been decrypted. Cybercriminals then thrive on the affected victims, who desperately want to get their files decrypted and safely returned, by demanding a ransom from them.
Locker ransomware, on the other hand, does not require data encryption. It simply prevents the user from using their computers or devices by locking them out. Once their access is blocked from their computers or devices, the cybercriminals will then demand a ransom in exchange for unlocking the devices.
Here are a few famous examples of ransomware:
- CryptoLocker
- Locky
- Jigsaw
- WannaCry
- Ryuk
- GandCrab
Read our blog on The Different Types of Ransomware to find out more about them.
Signs of Ransomware Infection
-
Splash Screen:
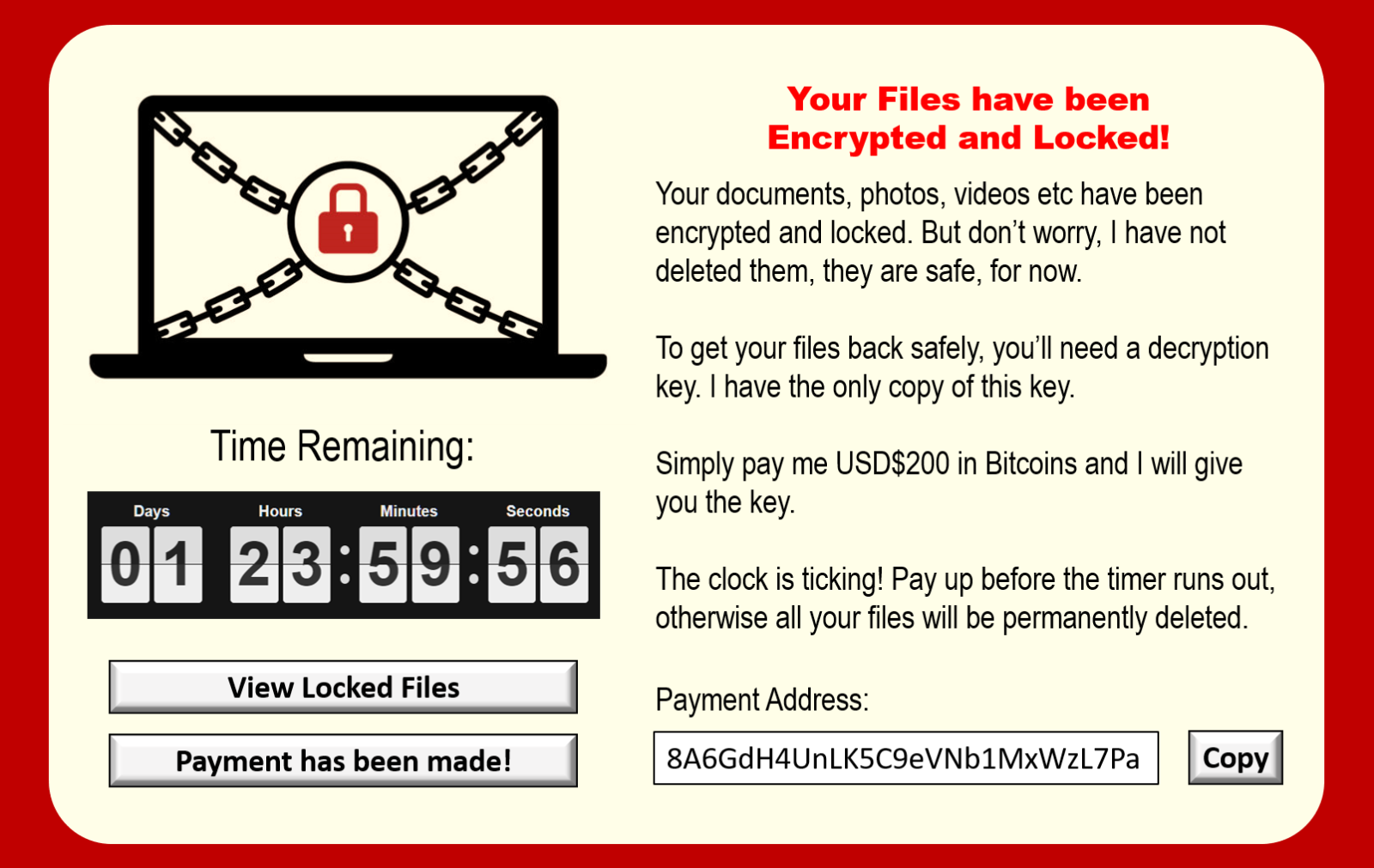
A splash screen is the most obvious sign of ransomware infection. These splash screens will typically appear upon computer or device startup, thereby preventing the user from accessing their computer or device. Instructions on how to pay the ransom will be provided as shown in the sample picture above.
-
Error Message When Opening Files:
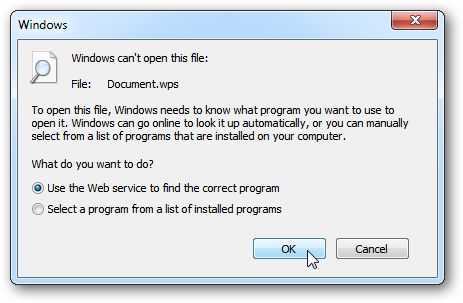
Error Message on Windows 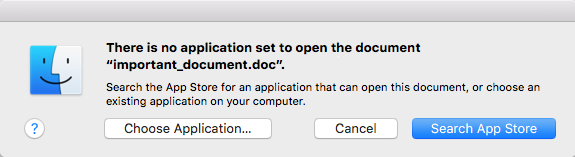
Error Message on Mac Error messages like the ones above are another sign of ransomware infection – specifically crypto ransomware. Such messages typically appear when opening individual documents on a computer or device.
-
Unusual File Extensions:
File Extensions refer to the suffix at the end of a filename, preceded by a full stop. These file extensions allow a computer or device to know what type of file it is. Some common examples of file extensions are “.pdf”, “.jpg”, “.doc” and “.txt”.
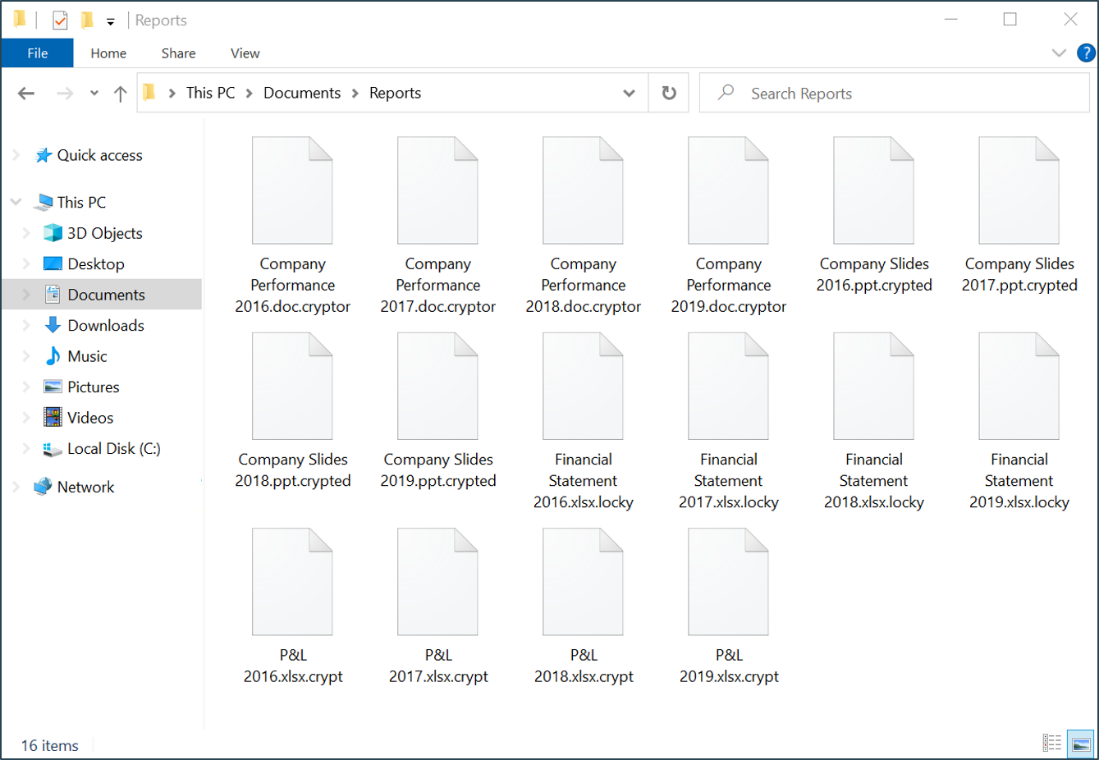
Ransomware encrypted files will have unusual file extensions or extensions that end with “.crypted”, “.cryptor” or “.crypt”. The file icon will usually be blank, like the ones shown above.
-
Files with Instructions on Paying the Ransom:
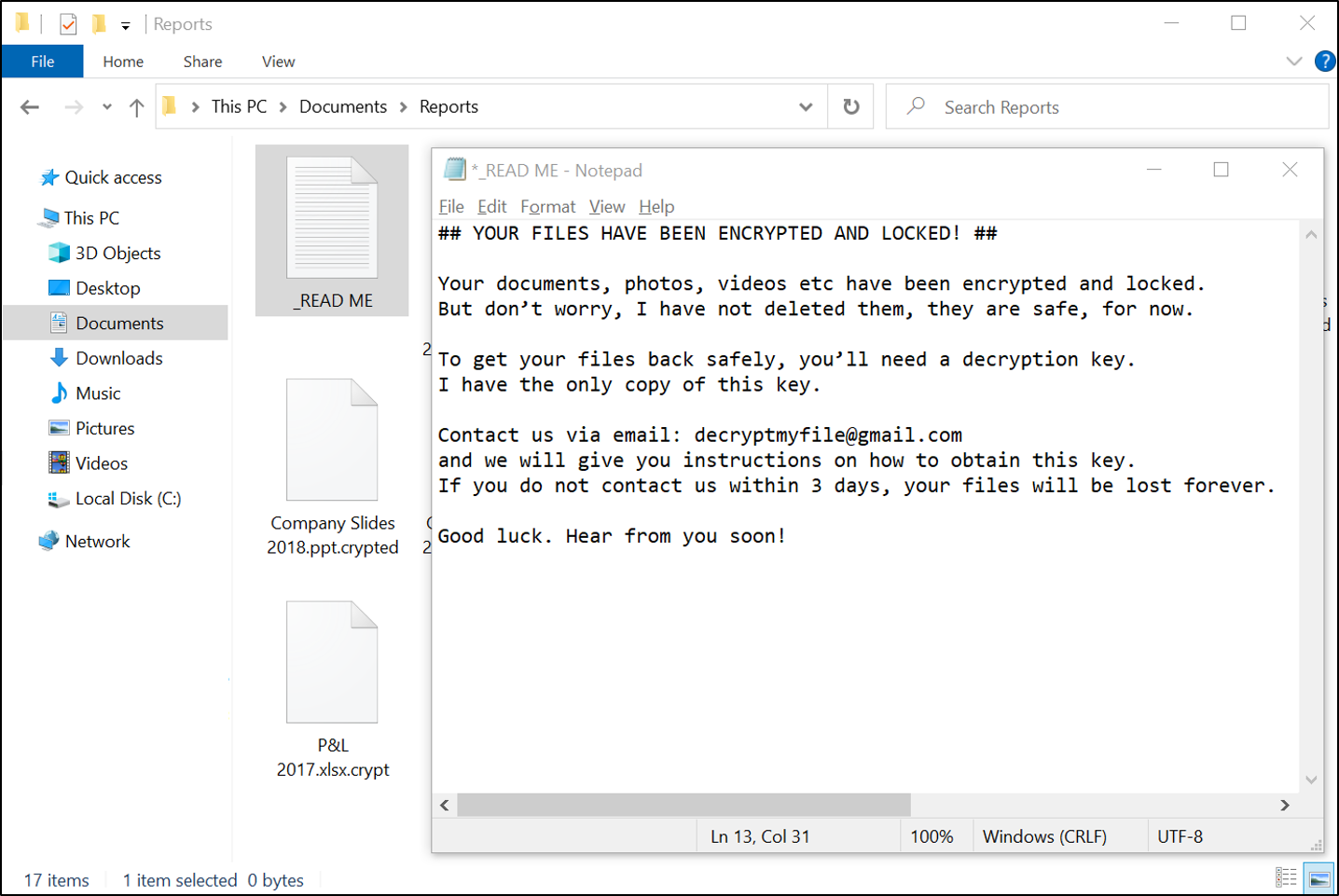
If a computer or device is infected by ransomware, it is common for the cybercriminal to leave instructions for the user to pay the ransom. After all, the main aim of planting ransomware is for the user to pay the cybercriminals.
To make these instruction files easily accessible, they will tend to be stored in every folder that has encrypted data. More often than not, these instructions are text documents with capitalized titles, preceded by an underscore. Some examples of the document titles are “_READ ME”, “_OPEN ME” and “_YOUR FILES HAVE BEEN ENCRYPTED”.
Preventing Ransomware
In order to find solutions on how to prevent a ransomware attack, we must always look for the root cause first. Most users who experienced a ransomware attack shared that they got infected by clicking on a link or opening an email attachment from unknown senders. Knowing this, here are some tips and precautions users can exercise to prevent falling prey to ransomware attacks:
-
Sender Verification:
It is good practice to check the sender of an email before opening any links or attachments associated with that email. Never open email links or attachments from unknown sources. If needed, contact a trusted IT professional to check on the email before opening any links or attachments.
-
Awareness:
Companies should spread awareness of ransomware by educating their employees about what it is and how to avoid being infected. This is a crucial precaution that most companies should take because ransomware can be easily prevented if every single computer user in a company is wary of it. All it takes is for one user to be at the mercy of these cybercriminals, and the entire company might be enmeshed in ransomware.
-
Effective Spam Filter:
On top of relying on its employees to be vigilant, companies should also take an extra precautionary measure too – ensuring that an effective spam filter is in place. An effective spam filter is one that is continuously updated. As technology is ever-evolving, so is ransomware, and likewise, spam filters should perpetually update themselves too. With an effective spam filter in place, suspicious emails can be blocked before even reaching the employees.
-
Endpoint Protection:
Endpoint Protection is a larger scale of antivirus. While antivirus software detects and blocks malicious files on a single computer or device, endpoint protection software protects an entire business network against different types of security threats. With endpoint protection software in place, different remote devices that are connected to the network, such as laptops and smartphones, will be protected. This acts as an extra step against ransomware attacks too as employees who are constantly on-the-go may access their emails via their smartphones.
-
Consistent Backup:
If a company’s data is continuously being backed up regularly, there will not be a need to pay for any ransom if a cybercriminal happens to plant ransomware in any of the companies’ computers. Lost data can be easily recovered, and the users will not be in the clutches of these cybercriminals.
Ransomware Recovery
In an unfortunate event that a company is being attacked by ransomware, they should seek help from IT companies that specializes in cybersecurity. Being experts in cybersecurity, these IT companies may have a decryption tool for the ransomware. One such company is Adventus.
On top of ransomware recovery, Adventus provides Managed Backup Services too. Our team of recovery specialists are equipped with and possess advanced tools, expertise, and experience to ensure that our clients’ systems or files are recovered within the shortest time possible (remotely or onsite) for them to achieve, and even improve, their recovery time objective.
To ensure that the backed-up data is working and not corrupted, Adventus Managed Backup Services includes monitoring services too. This means that all of our clients’ backup jobs and systems are being monitored religiously for errors, failures, resource constraints, and exceptions. When the need for file recoveries arise, our clients can be at ease and trust that they are able to restore the most recently backed-up version of their files.
In Conclusion
Even with all the precautionary measures taken against ransomware, there may still be a chance of an attack. Therefore, having consistent backup can “shield” companies from ransomware attacks. With proper and regular backup, companies that are infected by ransomware can easily restore their lost data in an unencrypted state.
At Adventus, we understand the business needs of our clients and will provide a Fully Managed Service that best fits their requirements. If you’re looking to improve the cybersecurity in your company, contact us now!
Recent Posts
- IT Outsourcing in Singapore
- Penetration Testing Explained: Think Like a Hacker, Stay Ahead of One
- Microsoft Teams Phone System: The Ultimate Solution for Modern Business Telephony
- Greener Prints, Greater Impact: Steps for Sustainable Printing at Work
- From Boardrooms to Classrooms: The Growing Role of Interactive Displays
- Microsoft 365 Phishing Threats Are Evolving – Are Your Defenses?
- Skype is Hanging Up — What’s Your Next Call?
- Last Call: Windows 10 End of Support Is Near — Secure Your Systems Now
- Business Broadband, Fibre, and You: A Complete Guide
- Cybersecurity Threats in 2024
- Best Outsource IT Support Services And Practices 2024
- Goodbye, Windows Server Update Services (WSUS): The IT Impacts of Microsoft’s Deprecation
- How To Get Cost-Efficient 24x7 IT Support in Singapore
- Countdown Begins: Windows 11 21H2 and 22H2 Support Ending in Less Than 2 Months
- CrowdStrike Cybersecurity Platform Faces Global Outage, Users Locked Out
- Latest Microsoft Outlook Security Update 2024 to Affect Accounts and Web Access
- Securing Your Systems: An Introduction to Patch Management
- 10 Great Tips for Selecting a Good Cybersecurity Company
- Tycoon 2FA: The Menacing MFA-Bypassing Phishing Threat Targeting Microsoft 365 and Gmail Accounts
- Fortinet Users Beware: New RCE Vulnerabilities Disclosed
- Ivanti Exploited: Third Zero-Day Vulnerability Uncovered (CVE-2024-21893)
- TeamViewer Exploited to Breach Vulnerable Networks and Deploy Ransomware
- Buying vs. Leasing vs. Renting A Copier / Printer in Singapore
- A Beginners Guide to Managed Cloud Backup Services
- Fortifying Your Digital Defence: The Importance of Multi-Factor Authentication
- 5 Advantages of Using Managed Backup Services
- New Phishing Method Discovered in Recent Cyber Attacks | Don’t Get Hooked!
- What Is IP Telephony, and How Can It Help Your Business?
- Zero Trust Network Access (ZTNA): What Is It and How It Transforms Your Network Security
- Embracing 24/7 Efficiency: Simplify Your Business with Future-Proof Cloud Print Solutions
- Cybersecurity Alert! Critical Vulnerabilities Found on Microsoft’s Outlook, Windows and Other Products
- 7 Factors to Consider When Outsourcing IT Support
- A Complete Guide to Door Access Control Systems
- Top 9 Password-Creating Tips That Will Change Your Life | Password Security
- Next Generation Firewall (NGFW) vs. Unified Threat Management (UTM) — Which is Best for You?
- Cloud PBX System: The Benefits of Using a Cloud Phone System for Business Communication
- Top 5 Benefits and Best Practices of Outsourcing IT Helpdesk Support
- Reducing Risks of Computer Virus Attacks in Hybrid Work Environments
- 3 Ways Your Company Can Benefit from Business Broadband
- Cybersecurity Threat: “Follina Vulnerability” Explained
- IP Phones vs. Analogue Phones
- On-site IT Support Services vs. Remote IT Support Services
- 5 Questions to Ask Yourself Before Creating A Ransomware Recovery Plan
- What To Look For When Choosing A Business Broadband
- 7 Cybersecurity Predictions for 2022
- Cybersecurity Threat: “Log4Shell Vulnerability” Explained
- What Is IT Support and What Does an IT Support Specialist Actually Do?
- Tips for Selecting a Good Door Access Control System
- Top 7 Reasons to Use Cloud Managed Backup Services
- A Complete Guide to Managed Cybersecurity Services
- Top 5 Financial Benefits of Managed IT Services
- The Different Types of Ransomware
- Ransomware Recovery in Singapore


