The Different Types of Ransomware
What is Ransomware?
Ransomware is a type of malicious software, or malware for short, that can limit or block users from accessing their files. By using this malware, cybercriminals can hold the user’s important documents as “hostages”. Users are then demanded to pay a ransom to free their documents – hence the term ransomware.
Types of Ransomware
In our earlier blog – Ransomware Recovery in Singapore, we have stated that ransomware can be broadly defined as two types: Crypto ransomware, which typically involves encryption to limit users’ access to files or data; and Locker ransomware, which functions by blocking users out of their computers or other devices.
Examples of Ransomware
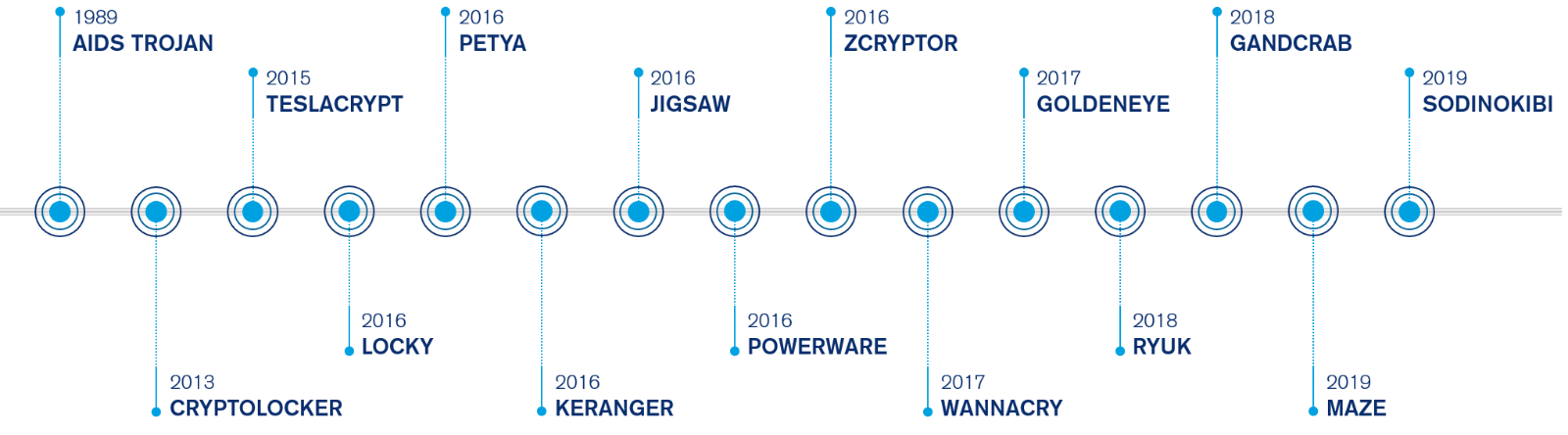
Now, let’s delve deeper into some of the different famous examples of ransomware:
-
CryptoLocker
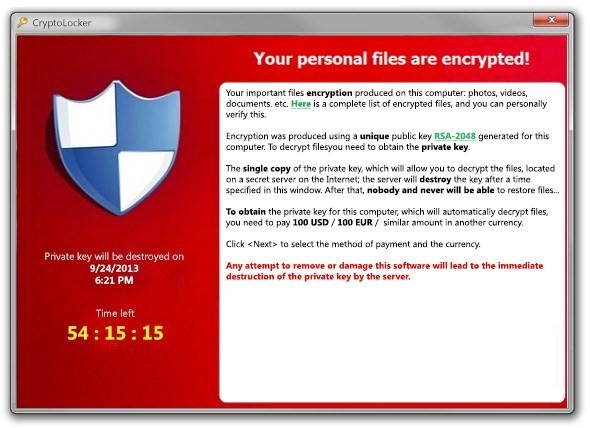
First emerged in 2013 – CryptoLocker is a malware that affects computers running on Windows. It is a Trojan horse malware that is often disguised as legitimate emails, thereby tricking many victims into downloading malicious attachments. Upon download, CryptoLocker will start crawling the hard drive and all other connected media, such as a shared network or a thumb drive, for valuable files and will encrypt them.
The cybercriminals behind CryptoLocker managed to infect around 500,000 computers (including those in law enforcement) and got away with an accumulative ransom of about USD$3 million.
Although the era of the CryptoLocker ended within a year, it was an inspiration to many cybercriminals. This marked the dawn of a new era of ransomware that varied from the concept of the CryptoLocker.
-
Locky
First emerged in 2016 – Locky is a comparatively complex type of ransomware with the capability of encrypting over 160 file types. It is usually sent as an email attachment disguised as a Microsoft Office document. Upon opening the attachment, there will be a prompt to enable Macros. By accepting this prompt, rather than enabling what was stated, it will instead allow Locky to run and start encrypting the victims’ files.
The group of organized cybercriminals behind Locky managed to infect around 400,000 computers within the first week and got away with an accumulative ransom of about USD$25 million till date.
Locky has constantly disappeared and re-emerged time and again. With each emergence, it will be updated, with improved features. At present, Locky is still an ongoing threat to unsuspecting victims.
-
KeRanger
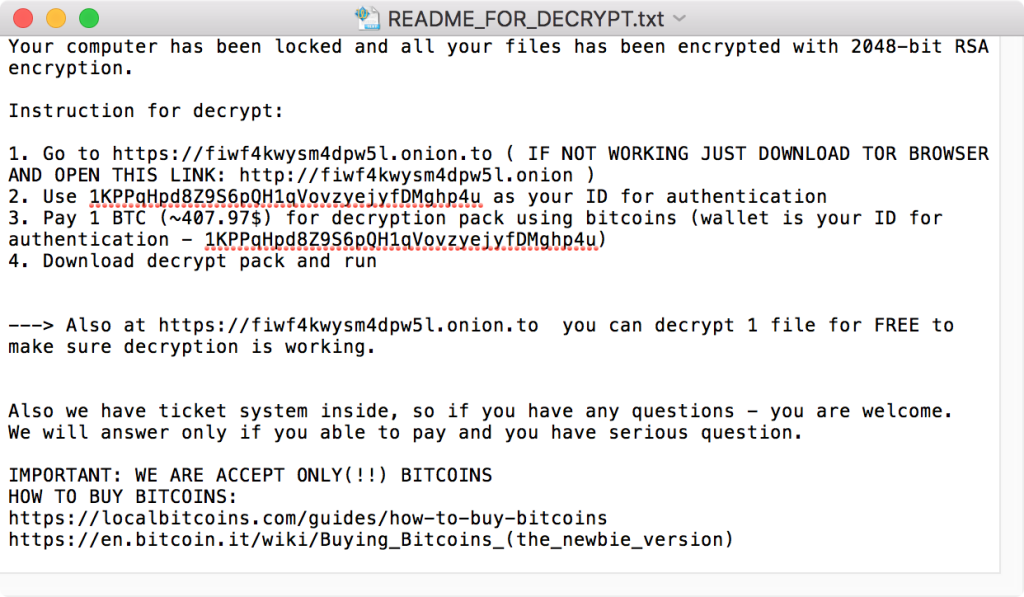
First emerged in 2016 – KeRanger is the first-ever fully functioning ransomware that affects computers running on Mac OS X. It can encrypt over 300 different file types!
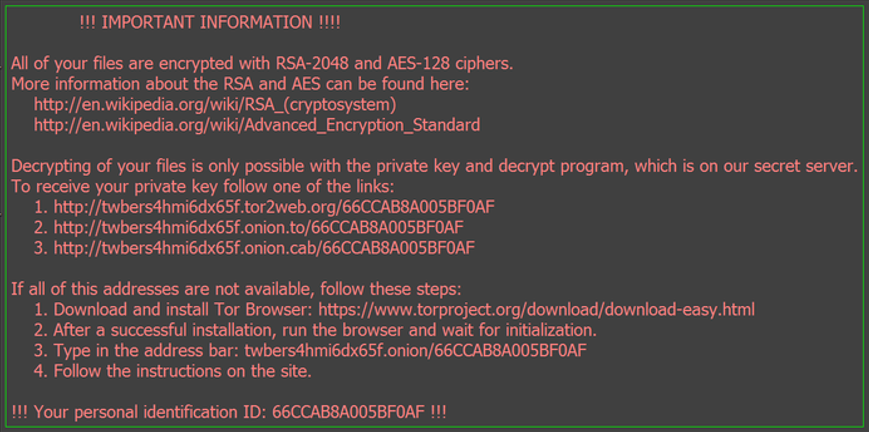
KeRanger was well hidden in a popular BitTorrent client application called Transmission. Upon downloading this application, the program files will be stored in the computer. One of these files, titled “General.rtf”, was the executable malware, nicely disguised as a rich-text file. This malware stays dormant for the first three days of download. After which, it will be activated and starts encrypting files. A “ReadMe” text document, like the one above, is then saved in every single folder where files have been encrypted. The encrypted files will not be accessible until the ransom has been paid in the form of cryptocurrency, known as Bitcoins.
Upon discovery of this hidden malware, Transmission has since updated its application to remove KeRanger. Apple has also added new security features to prevent the installation of applications that do not have a valid developer ID.
-
Jigsaw
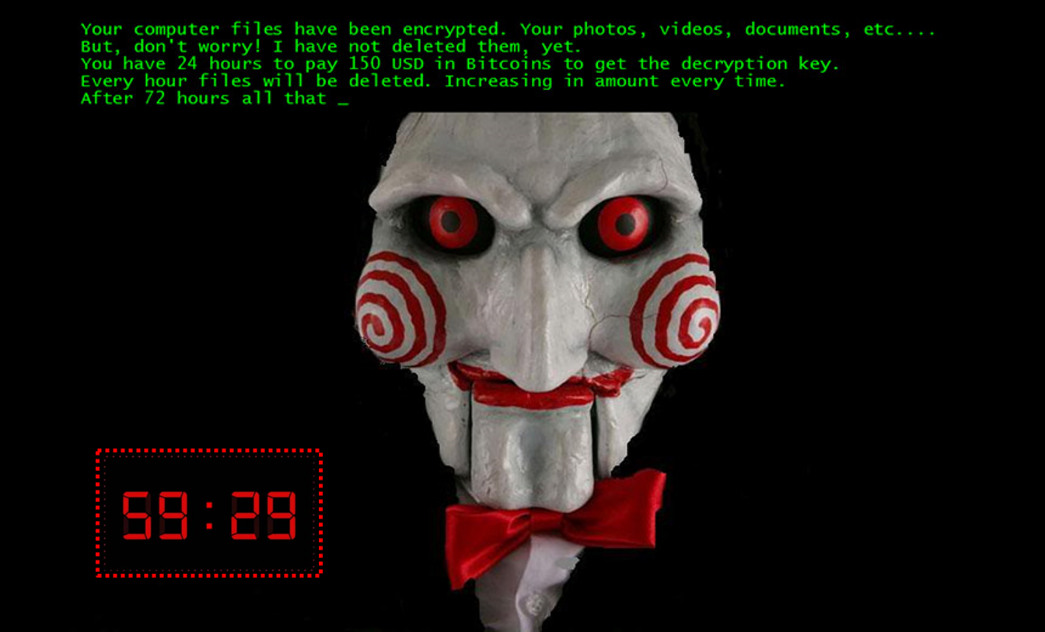
First emerged in 2016 – Jigsaw is a ransomware named after the puppet from the film franchise ‘Saw’, because its prompt for ransom displays the puppet’s face, like in the image above. It can encrypt around 226 different file types!
Unlike other ransomware that merely threatened to delete files, Jigsaw is the first ransomware that actually carried out the threat and started deleting files progressively as time passes if the ransom requirements are not met.
When a user is infected with Jigsaw, a countdown timer will start. If the ransom amount stated is not paid, it will start deleting the files – starting with one file every hour to gradually increasing the number of files deleted every hour. In addition, if the user attempts to tamper with the ransomware or restart the infected computer, Jigsaw will carry out a “punishment” by automatically deleting as many as 1,000 files!
Due to the cruel nature of this malware, Jigsaw has caused several companies to lose huge amounts of money as a result of data loss. At present, Jigsaw is still an ongoing threat to unsuspecting victims.
-
WannaCry
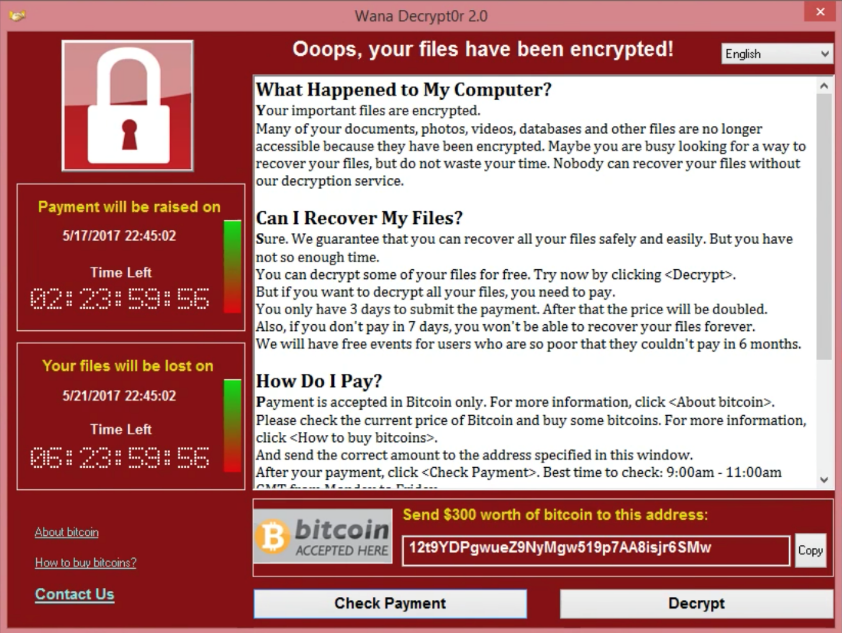
First emerged in 2017 – WannaCry affects computers operating on Microsoft Windows. It exploited the fact that users are slow in updating / patching their operating systems. Those who did not update the latest Microsoft patch had their data encrypted and received demands for ransom in the form of Bitcoins.
The WannaCry wave hit for about 4 days and the cybercriminals behind WannaCry managed to infect around 230,000 computers globally (including high-profile systems like government systems and railway networks) and got away with an accumulative ransom of more than USD$4 billion.
-
Ryuk
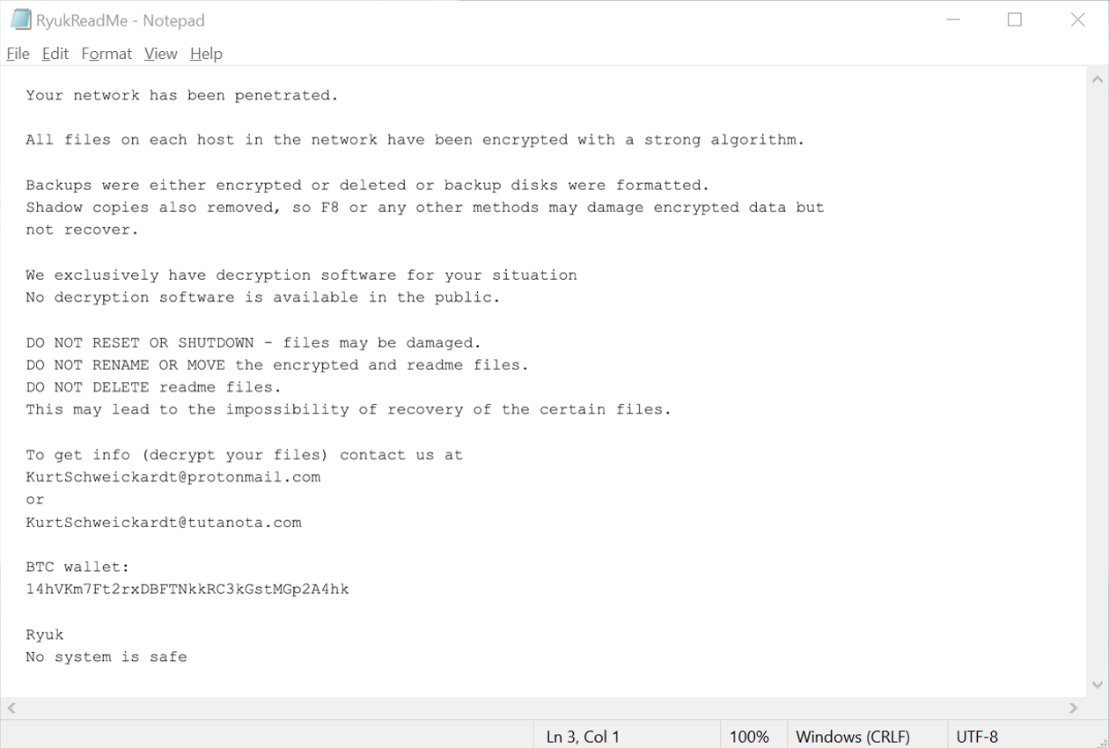
First emerged in 2018 – Ryuk is a “targeted ransomware” that chooses its victims to attack. Instead of the usual massive spamming method of spreading a ransomware, the cybercriminals behind Ryuk went with a more targeted approach. Their pre-selected victims will be companies who are more likely to pay to restore their data since they have a lot on the line.
Once targeted, Ryuk can silently infiltrate the system and lurk in the background for weeks, observing and waiting for the right time to strike so as to maximize its impact. While lurking, it can also disable the Windows System Restore option, making it impossible to recover encrypted files if they were not backed-up externally.
Due to its highly selective nature, the cybercriminals behind Ryuk managed to get away with an accumulative ransom of around USD$3.7 million in just 52 payments
-
GandCrab
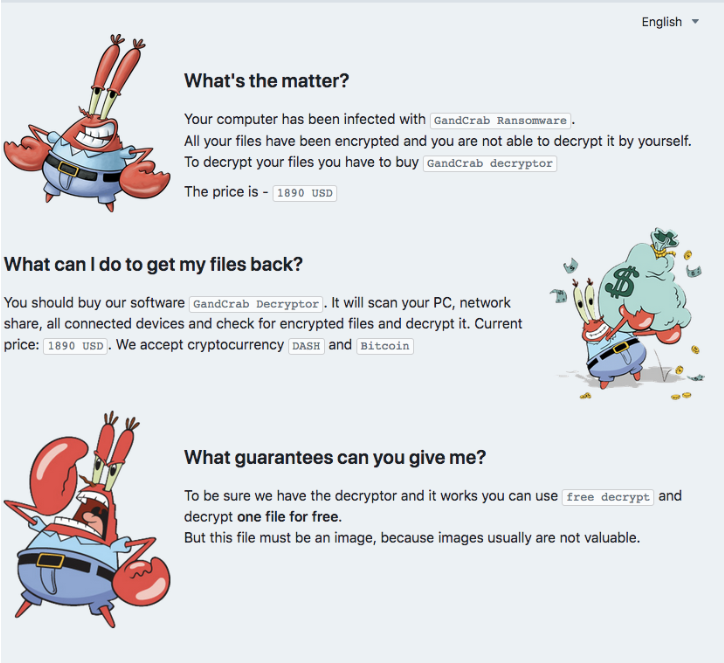
First emerged in 2018 – GandCrab is a Crypto ransomware that targets computers running on Microsoft Windows. When attacked, users get a note like the one above, asking them to buy the GandCrab decryption tool. It also allows them to decrypt one file for free, to prove that the provided decryption tool works.
GandCrab uses a Ransomware-as-a-Service (RaaS) model whereby the developers sell RaaS packages to cybercriminal who do not have much technical coding knowledge. These “cybercriminal wannabes” can purchase a specific ransomware via a subscription-based model (pay the developers a monthly subscription fee) or an affiliate model (pay the developers a percentage of the ransom that they have collected). This way, GandCrab was able to spread far and wide while the developers continued tinkering and improving on it.
With this RaaS model, the cybercriminals behind GandCrab managed to infect around 1.5 million devices and got away with about USD$2 billion. To add a dash of humour, the later versions of GandCrab featured Mr. Krabs from Spongebob Squarepants, the popular animated television series. They even offered “free 24/7 online chat support” for victims facing any issues with paying the ransom or downloading their decryption tool.
Thankfully, the cybercriminals behind GandCrab had announced their “retirement” in 2019, giving us one less ransomware to worry about.
What to Do When Infected by Ransomware?
-
Isolate the Infection by Disconnecting the Affected Device
Cutting the infection off is the most crucial step to prevent the ransomware from spreading to other devices connected to the infected computer. This can be done by:
- Disconnecting from the Internet (Wired or Wireless)
- Disconnecting from any Wireless Network or Network Cables
- Removing any Portable Storage Devices
-
Take a Picture of the Ransom Note
It is best to use a different device like a mobile phone to take a photo of the ransom note being displayed on the screen of the affected device. This picture will come in handy when reporting to the authorities or when seeking help from a professional.
-
Restore from Backup
If there are consistent backup policies in place, the lost data can be easily restored. Simply head over to the IT department to have the data safely restored. With the worry of data loss off your mind, it’ll be easier to focus on tracking the ransomware and removing it totally.
-
Seek Help from a Cybersecurity Professional
It is best to seek help from a cybersecurity professional to ensure that there is no trace of the ransomware left in the affected computer or in the network that it was connected to. The photo that was taken in Step #2 will be a very helpful piece of information to share with the professional. This can help them determine the approach that they should take to get rid of the ransomware.
In addition, if the lost data cannot be restored, these cybersecurity experts will usually have a decryption tool for the ransomware. These cybersecurity experts and professionals refer to IT companies that specializes in cybersecurity. They are well-equipped with advanced tools and have a team of well-trained specialists.
The last thing any business want is to have their important data locked away or even deleted by cybercriminals. Fortunately, Adventus is one of those IT companies that specializes in cybersecurity. We can help decrypt encrypted files, provide root cause analysis on the affected devices as well as protect against ransomware. Be sure to contact us for more information on how to improve your IT Security today!
Recent Posts
- IT Outsourcing in Singapore
- Penetration Testing Explained: Think Like a Hacker, Stay Ahead of One
- Microsoft Teams Phone System: The Ultimate Solution for Modern Business Telephony
- Greener Prints, Greater Impact: Steps for Sustainable Printing at Work
- From Boardrooms to Classrooms: The Growing Role of Interactive Displays
- Microsoft 365 Phishing Threats Are Evolving – Are Your Defenses?
- Skype is Hanging Up — What’s Your Next Call?
- Last Call: Windows 10 End of Support Is Near — Secure Your Systems Now
- Business Broadband, Fibre, and You: A Complete Guide
- Cybersecurity Threats in 2024
- Best Outsource IT Support Services And Practices 2024
- Goodbye, Windows Server Update Services (WSUS): The IT Impacts of Microsoft’s Deprecation
- How To Get Cost-Efficient 24x7 IT Support in Singapore
- Countdown Begins: Windows 11 21H2 and 22H2 Support Ending in Less Than 2 Months
- CrowdStrike Cybersecurity Platform Faces Global Outage, Users Locked Out
- Latest Microsoft Outlook Security Update 2024 to Affect Accounts and Web Access
- Securing Your Systems: An Introduction to Patch Management
- 10 Great Tips for Selecting a Good Cybersecurity Company
- Tycoon 2FA: The Menacing MFA-Bypassing Phishing Threat Targeting Microsoft 365 and Gmail Accounts
- Fortinet Users Beware: New RCE Vulnerabilities Disclosed
- Ivanti Exploited: Third Zero-Day Vulnerability Uncovered (CVE-2024-21893)
- TeamViewer Exploited to Breach Vulnerable Networks and Deploy Ransomware
- Buying vs. Leasing vs. Renting A Copier / Printer in Singapore
- A Beginners Guide to Managed Cloud Backup Services
- Fortifying Your Digital Defence: The Importance of Multi-Factor Authentication
- 5 Advantages of Using Managed Backup Services
- New Phishing Method Discovered in Recent Cyber Attacks | Don’t Get Hooked!
- What Is IP Telephony, and How Can It Help Your Business?
- Zero Trust Network Access (ZTNA): What Is It and How It Transforms Your Network Security
- Embracing 24/7 Efficiency: Simplify Your Business with Future-Proof Cloud Print Solutions
- Cybersecurity Alert! Critical Vulnerabilities Found on Microsoft’s Outlook, Windows and Other Products
- 7 Factors to Consider When Outsourcing IT Support
- A Complete Guide to Door Access Control Systems
- Top 9 Password-Creating Tips That Will Change Your Life | Password Security
- Next Generation Firewall (NGFW) vs. Unified Threat Management (UTM) — Which is Best for You?
- Cloud PBX System: The Benefits of Using a Cloud Phone System for Business Communication
- Top 5 Benefits and Best Practices of Outsourcing IT Helpdesk Support
- Reducing Risks of Computer Virus Attacks in Hybrid Work Environments
- 3 Ways Your Company Can Benefit from Business Broadband
- Cybersecurity Threat: “Follina Vulnerability” Explained
- IP Phones vs. Analogue Phones
- On-site IT Support Services vs. Remote IT Support Services
- 5 Questions to Ask Yourself Before Creating A Ransomware Recovery Plan
- What To Look For When Choosing A Business Broadband
- 7 Cybersecurity Predictions for 2022
- Cybersecurity Threat: “Log4Shell Vulnerability” Explained
- What Is IT Support and What Does an IT Support Specialist Actually Do?
- Tips for Selecting a Good Door Access Control System
- Top 7 Reasons to Use Cloud Managed Backup Services
- A Complete Guide to Managed Cybersecurity Services
- Top 5 Financial Benefits of Managed IT Services
- The Different Types of Ransomware
- Ransomware Recovery in Singapore


