Microsoft 365 Phishing Threats Are Evolving – Are Your Defenses?

Phishing scams are getting smarter — and more expensive. Instead of the obvious phishing emails we’re used to, cybercriminals now impersonate trusted entities like Microsoft, tricking organizations into sending money, sharing sensitive data, or handing over login credentials. The statistics are concerning: Forbes reports that over half of companies globally experienced a phishing attack in just the first quarter of 2024.
Microsoft 365 has become a prime target due to its widespread use and the sensitive data it holds. A report by CheckPoint found that Microsoft was the most impersonated brand in phishing attacks, making up 32% of such attempts in late 2024. But these scams go beyond simple lookalike emails — cybercriminals are finding new ways to exploit Microsoft 365’s own infrastructure to bypass email security measures and make their cybercriminals appear completely legitimate.
So how exactly are they doing it? Let’s break it down.
How Microsoft 365 Phishing Attacks Unfold
-
Taking Over Microsoft 365 Accounts
Instead of sending fake emails from random domains, attackers take a more sophisticated approach. They register real Microsoft 365 business accounts (tenants) or take over existing ones. Each account serves a different purpose in their scam:
- Tenant 1: Generates real-looking purchase receipts
- Tenant 2: Impersonates a trusted company like Microsoft
- Tenant 3: Reroutes emails to avoid email security detection
This layered approach makes it incredibly hard to track and make their emails look completely authentic.
-
Manipulating Microsoft 365 Settings
First, cybercriminals will create new administrative accounts under the “*.onmicrosoft.com” domain. Since these accounts don’t use corporate email domains, they blend in with Microsoft’s default system settings and avoid raising red flags.
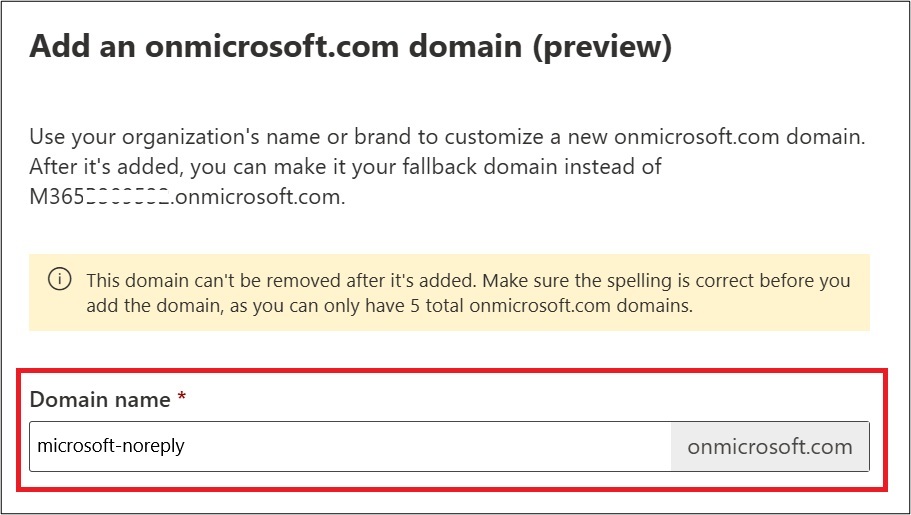
Next, they set up email forwarding rules to intercept and redirect security alerts. By silently rerouting critical notifications, they ensure that IT teams are kept in the dark about any suspicious activity.
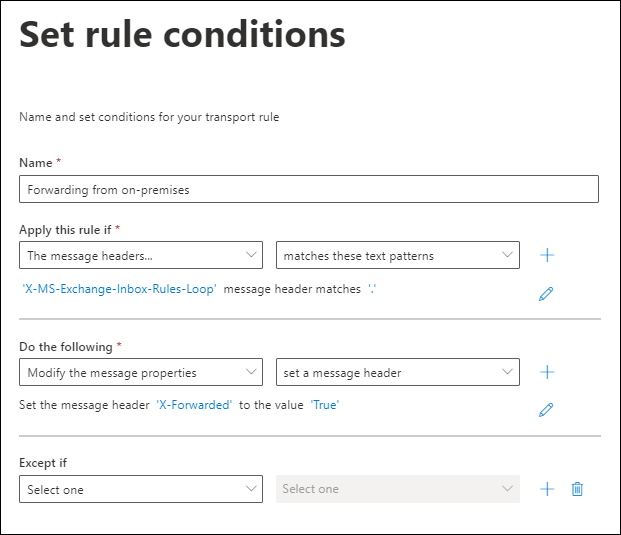
Finally, they modify display names to make phishing emails appear as though they are coming from Microsoft. This subtle manipulation enhances credibility, making victims more likely to trust the fraudulent messages.
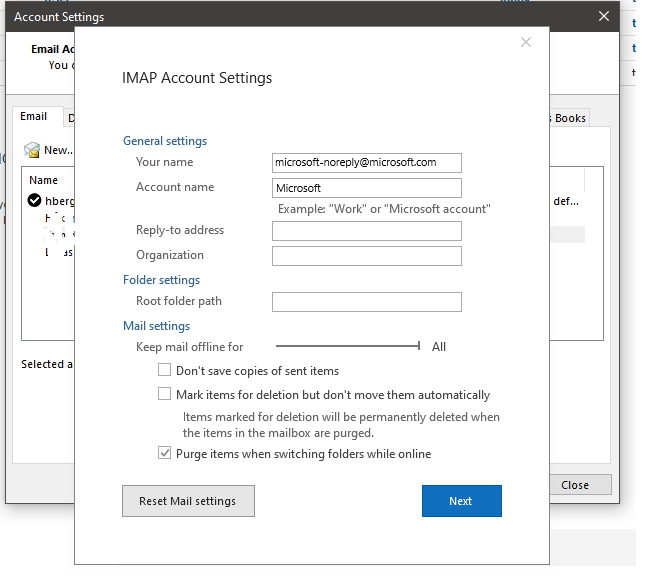
As a result, when a victim receives an email, it originates from an actual Microsoft system, not an unverified external server, bypassing traditional email security measures and increasing the likelihood of a successful attack.
-
The Perfect Scam Email
Instead of sending obvious phishing emails, cybercriminals manipulate Microsoft’s system to send a real email that includes fake details.
A victim might receive a deceptive email like:
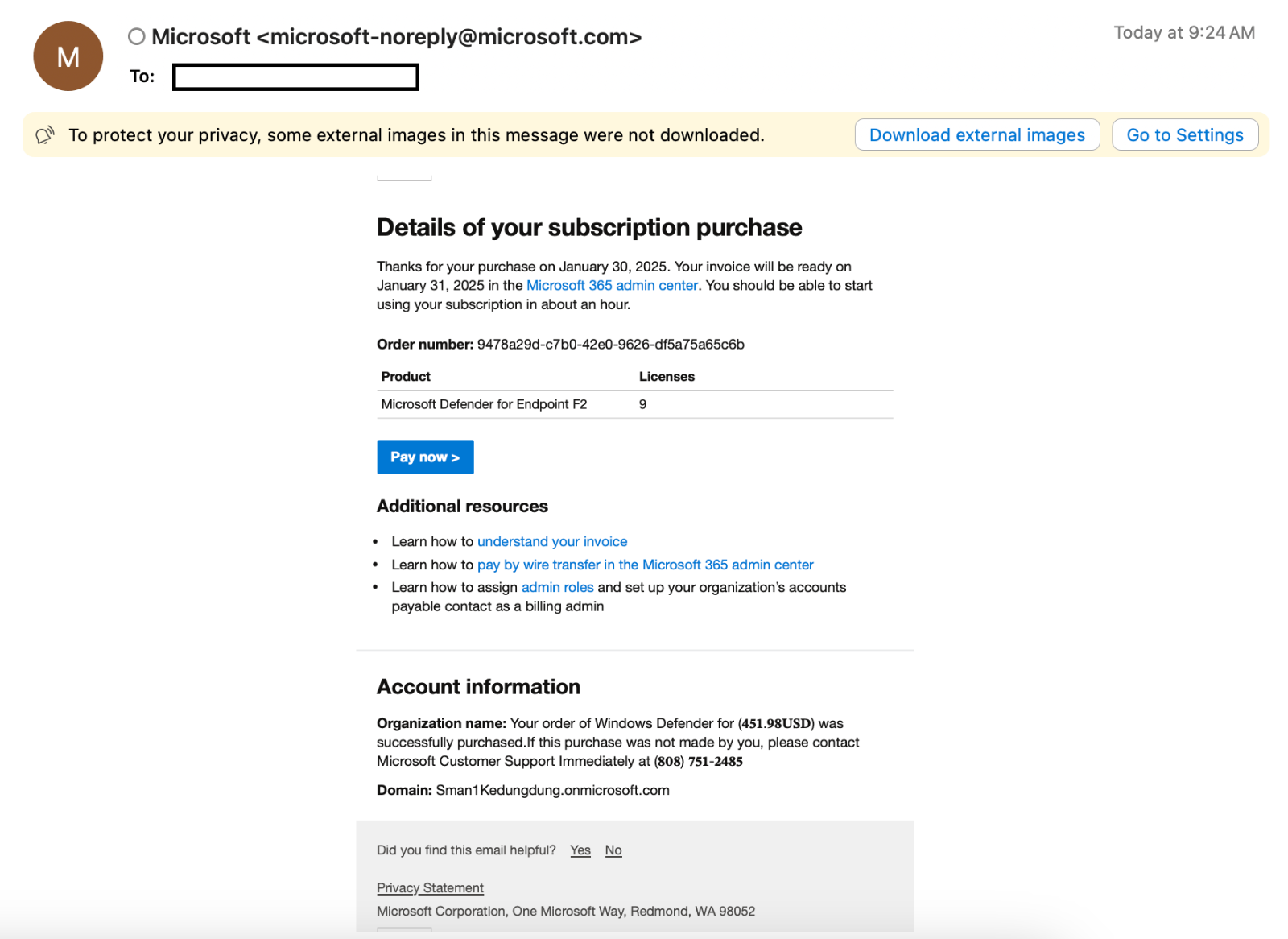
Because this alert originates from the official Microsoft.com domain, it bypasses email security filters and appears entirely legitimate to the victim.
-
The Trap is Set
Believing the email is legitimate, the victim takes the bait — either by clicking the link or calling the provided number — without realizing they are stepping into the cybercriminal’s trap.
If they click the link, they are redirected to a fake Microsoft login page designed to steal their credentials. The page looks nearly identical to the real one, tricking them into entering their username and password. If they call the number, a scammer posing as Microsoft support will attempt to extract sensitive information or persuade them to install malicious software.
Victims could detect the scam by logging into their Microsoft 365 account and checking their billing history to confirm if the subscription was actually made. Unfortunately, most people don’t take this extra step before reacting. Because the email appears so authentic, many victims unknowingly hand over their credentials or expose their systems to further attacks.

Why This Attack Works So Well
Traditional phishing emails often contain red flags: fake domains, suspicious links, or unknown senders. But Microsoft 365 phishing attacks are far more deceptive because they exploit Microsoft’s own infrastructure. These emails don’t just look real; they are real, coming from actual Microsoft accounts and services.
By hijacking legitimate Microsoft 365 tenants, cybercriminals bypass spam filters and email security gateways that would typically block phishing attempts. Because these emails originate from trusted sources, they land directly in inboxes, making detection nearly impossible.
Additionally, the cybercriminals use familiar workflows — OneDrive file shares, invoice notifications, or security alerts — that employees encounter daily. Since the messaging aligns with what users expect to receive, they are more likely to trust and act on it without suspicion.
The combination of authenticity, familiarity, and technical manipulation makes the Microsoft 365 attack one of the most dangerous phishing methods today.
Traditional Security Isn’t Enough Anymore
Many businesses still rely on basic security measures like perimeter firewalls, standard antivirus software, and rule-based email security filtering. While these tools provide a foundational level of protection, they are no longer enough to stop today’s advanced cyberattacks. If cybercriminals are leveraging Microsoft’s own infrastructure to bypass defenses, organizations must rethink their approach to cybersecurity.
To counter these evolving threats, businesses need a modern cybersecurity approach that includes real-time threat detection, proactive security monitoring, and continuous vulnerability assessments. More importantly, cybersecurity awareness training ensures that employees recognize these sophisticated attacks before they fall victim.
Protect Your Business with Adventus
A strong defense requires a multi-layered strategy. At Adventus, we provide end-to-end Cybersecurity Solutions and Services to safeguard your business against Microsoft 365 phishing attacks at every level. Our advanced Microsoft 365 Security Management Services safeguard your environment by continuously monitoring for suspicious activities, preventing unauthorized access, and securing user accounts against exploitation. By proactively managing security policies, detecting anomalies, and responding to threats in real time, we help close the gaps attackers seek to exploit.
To further fortify your defenses, Adventus helps you establish strict access controls, ensuring that only verified users can reach critical systems — shutting down phishing attempts before they even begin. Our approach extends beyond access management; we secure every endpoint, shielding devices from hidden malware that attackers use to gain a foothold. Meanwhile, our Security Operations Centre (SOC) works around the clock, detecting and neutralizing threats in real time so risks are stopped before they escalate.
Beyond technology, we equip employees with cybersecurity awareness training to recognize and avoid deceptive emails, strengthening your first line of defense.
Don’t wait until an attack happens. Contact Adventus today to reinforce your Microsoft 365 security and keep your business protected.
Recent Posts
- IT Outsourcing in Singapore
- Penetration Testing Explained: Think Like a Hacker, Stay Ahead of One
- Microsoft Teams Phone System: The Ultimate Solution for Modern Business Telephony
- Greener Prints, Greater Impact: Steps for Sustainable Printing at Work
- From Boardrooms to Classrooms: The Growing Role of Interactive Displays
- Microsoft 365 Phishing Threats Are Evolving – Are Your Defenses?
- Skype is Hanging Up — What’s Your Next Call?
- Last Call: Windows 10 End of Support Is Near — Secure Your Systems Now
- Business Broadband, Fibre, and You: A Complete Guide
- Cybersecurity Threats in 2024
- Best Outsource IT Support Services And Practices 2024
- Goodbye, Windows Server Update Services (WSUS): The IT Impacts of Microsoft’s Deprecation
- How To Get Cost-Efficient 24x7 IT Support in Singapore
- Countdown Begins: Windows 11 21H2 and 22H2 Support Ending in Less Than 2 Months
- CrowdStrike Cybersecurity Platform Faces Global Outage, Users Locked Out
- Latest Microsoft Outlook Security Update 2024 to Affect Accounts and Web Access
- Securing Your Systems: An Introduction to Patch Management
- 10 Great Tips for Selecting a Good Cybersecurity Company
- Tycoon 2FA: The Menacing MFA-Bypassing Phishing Threat Targeting Microsoft 365 and Gmail Accounts
- Fortinet Users Beware: New RCE Vulnerabilities Disclosed
- Ivanti Exploited: Third Zero-Day Vulnerability Uncovered (CVE-2024-21893)
- TeamViewer Exploited to Breach Vulnerable Networks and Deploy Ransomware
- Buying vs. Leasing vs. Renting A Copier / Printer in Singapore
- A Beginners Guide to Managed Cloud Backup Services
- Fortifying Your Digital Defence: The Importance of Multi-Factor Authentication
- 5 Advantages of Using Managed Backup Services
- New Phishing Method Discovered in Recent Cyber Attacks | Don’t Get Hooked!
- What Is IP Telephony, and How Can It Help Your Business?
- Zero Trust Network Access (ZTNA): What Is It and How It Transforms Your Network Security
- Embracing 24/7 Efficiency: Simplify Your Business with Future-Proof Cloud Print Solutions
- Cybersecurity Alert! Critical Vulnerabilities Found on Microsoft’s Outlook, Windows and Other Products
- 7 Factors to Consider When Outsourcing IT Support
- A Complete Guide to Door Access Control Systems
- Top 9 Password-Creating Tips That Will Change Your Life | Password Security
- Next Generation Firewall (NGFW) vs. Unified Threat Management (UTM) — Which is Best for You?
- Cloud PBX System: The Benefits of Using a Cloud Phone System for Business Communication
- Top 5 Benefits and Best Practices of Outsourcing IT Helpdesk Support
- Reducing Risks of Computer Virus Attacks in Hybrid Work Environments
- 3 Ways Your Company Can Benefit from Business Broadband
- Cybersecurity Threat: “Follina Vulnerability” Explained
- IP Phones vs. Analogue Phones
- On-site IT Support Services vs. Remote IT Support Services
- 5 Questions to Ask Yourself Before Creating A Ransomware Recovery Plan
- What To Look For When Choosing A Business Broadband
- 7 Cybersecurity Predictions for 2022
- Cybersecurity Threat: “Log4Shell Vulnerability” Explained
- What Is IT Support and What Does an IT Support Specialist Actually Do?
- Tips for Selecting a Good Door Access Control System
- Top 7 Reasons to Use Cloud Managed Backup Services
- A Complete Guide to Managed Cybersecurity Services
- Top 5 Financial Benefits of Managed IT Services
- The Different Types of Ransomware
- Ransomware Recovery in Singapore


